Social engineering is the attempt to influence a person’s behavior to coerce them into a desired action through psychological influence.
In the context of IT it is a type of malicious attack with the goal of obtaining or accessing confidential information of an institution or individual. This is achieved by the exploitation of emotional vulnerabilities, usually motivated by financial gain.

According to the World Economic Forum 95% of cyberattacks are due to some kind of human error, making humans the most popular cyberattack vector.
The 3 most common social engineering methods
Social engineering attacks typically try to convince their victim via some sort of message to open a link, attachment, or to download malware and provide their login credentials. To achieve this, attackers use a combination of deceitful practices with the goal to acquire sensitive data or to get access to a system. The most common are the following:
Phishing
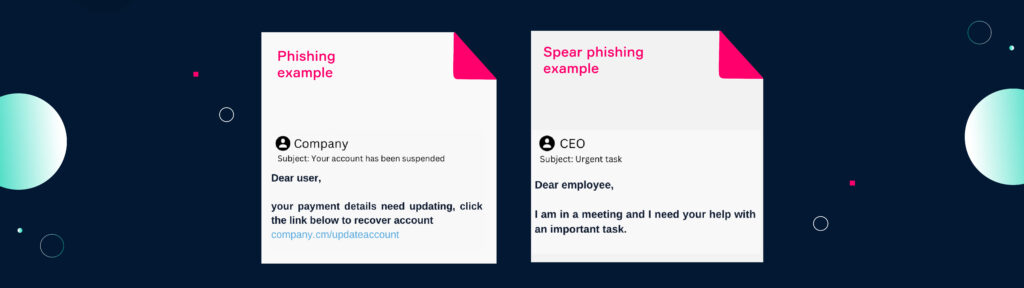
Phishing is the most common form of social engineering and the most common cyberattack. Via a message recipients are tricked into revealing personal information or to open an attached file. There are many different forms of phishing, depending on the vector and vulnerability exploited. E-mail is the most common channel accounting for 96% of total attacks.
Phishing attacks can target a wide-range of people or specific individuals. Normal phishing attempts are broad attacks that require less research about an individual. They leverage large databases to send out automated mass messages with the idea that some people might fall for it. Spear phishing, in contrast, is a targeted attack directed towards a specific individual or organizational structure. By thoroughly researching their target, attackers have, therefore, a much higher success rate.
Spoofing
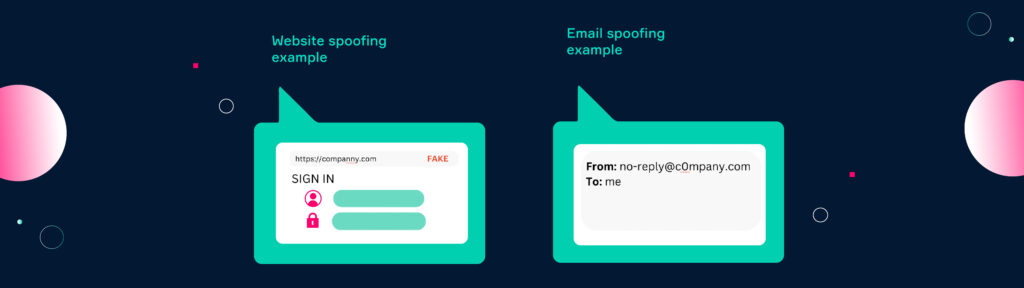
Spoofing occurs when a malicious actor tries to impersonate a trusted organization or individual. This is done by mimicking the identity, phone number, domain name, or IP address of the original source. Spoofing attempts often use e-mail addresses with similar domain names, copied phone numbers, or fake IP addresses. Depending on the level of hacking expertise, spoofing attempts can come very close or are sometimes even indistinguishable from the original source.
Pretexting
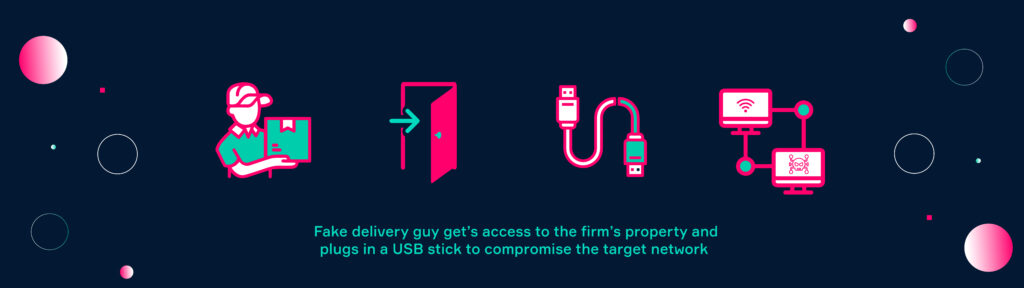
Pretexting is a situation in which attackers create a fake scenario that pressures their target to act according to their interest. The attacker typically pretends to be an authoritative figure that needs specific information from its target or access to a restricted area. Pretexting exploits the fact that people tend to listen and follow when an authority tells them to do so. These authorities can be the classic police investigator but also individuals that have authority due to their job requirement such as a mail carrier.
How does a social engineering attack happen?
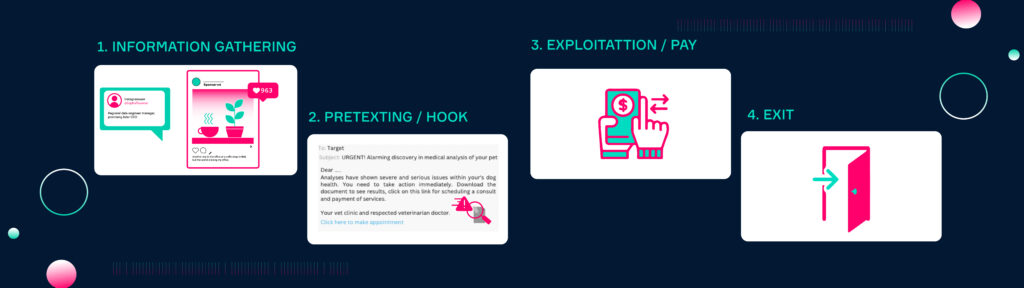
- Information gathering: Attackers conduct research about potential victims and attack paths. Depending on the approach, a wide or specific target audience is selected. All publicly available information is gathered (OSINT) in order to develop an attack scenario with a high probability of success.
- Pretexting / Hook: The attacker impersonates a trusted figure and creates a fake scenario to engage his target.
- Exploitation / Pay: The attack is executed. The victim is tricked into a certain action and exploited. The attacker achieves his goal.
- Exit: The attacker covers all his tracks and exits the interaction, leaving the victim before it realizes what happened.
Final thoughts
The cost of performing a social engineering attack is low, the effects devastating. Compared to other cyberattacks malicious actors have only low to moderate risk of getting caught, while the potential benefits are substantial. This is what makes it the most common cybercrime and one of the biggest cybersecurity threats for any organization or private individual. Social engineering is so effective because it circumvents many security measures by exploiting human errors. This is why these types of attacks have to be taught to the general public so that damages can be avoided.
