Websites and web applications (web apps), such as online shops or online banks, have become an integral part of the everyday lives of most internet users. Nowadays, more than 1.9 billion websites are using a variety of web applications for all kinds of interactions. Easy access without prior installation contributed to the growing popularity of web apps. However, public accessibility has made web applications a popular target for malicious attackers.
A web app pentest identifies vulnerabilities and provides recommendations how to improve a web application’s security. This can be, for example, the login authentication of an online banking app. In these tests IT security experts provide a realistic simulation of a hacking attack. The difference is that penetration testers only assess if web application has vulnerabilities, they don’t abuse them for malicious purposes.

How does a web application work?
Web applications function according to the client-server model. They do not have to be downloaded, instead they are deployed on a web server. They are accessible by any kind of internet capable device (client) that is able to use an internet browser, such as Google Chrome, Edge, Safari, and Firefox.
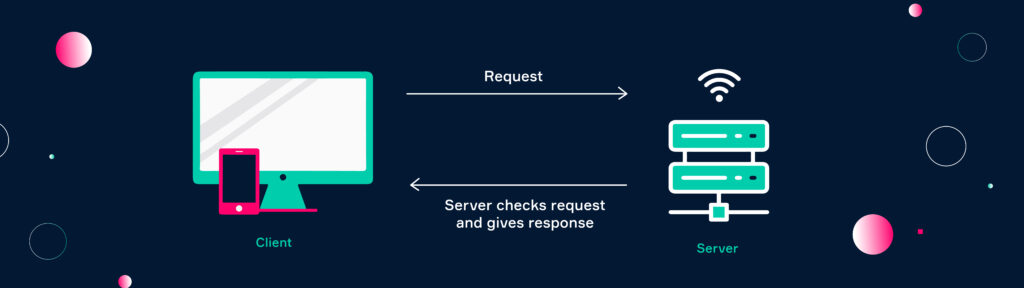
Web apps are easy to update and maintain. Instead of thousand of device, a web app runs on one server infrastructure. The benefit of this setup is that web apps only have to make sure to work on the most common browsers. Also, the devices accessing the web app do not need a lot of processing power as the computing processes take place on the server of the web application. The user performs and action via the user interface of the browser (front end), the requests are handled by the server (back end).
There is a catch with web applications though. The communication between client, web app, and web server is a very attractive target for malicious actors. Security is, therefore, key.
Why is a web application penetration test necessary?
Cyberattacks are on the rise. Web applications are an attractive target as they are publicly accessible. A web application penetration test helps to identify vulnerabilities in a web application that attackers could exploit.
Example web app vulnerabilities and their effects:
- SQL injection – Enables attackers to access or modify sensitive data in the data base of a web application due to user input not being properly validated when running SQL queries.
- Cross-Site Scripting (XSS) – Allows attackers to inject their own malicious scripts into a website. These scripts are able to access cookies, session tokens, or other sensitive information used by the browser and with the website.
Web apps and their associated servers use and store sensitive data, such as account balances, names, and addresses of bank customers. A successful cyber attack against a web application can thus cause huge data losses and financial damages. A penetration test enables an in-depth and realistic analysis of the current state of an application’s security. For this reason, e.g. banks, hospitals, energy providers and other parts of critical infrastructure are obliged to conduct annual penetration tests for their IT infrastructure and web applications.
How does a web application penetration test work?
In a web app pentest a cybersecurity expert assesses the security posture of a web application. The focus of this assessment lies in analyzing how the web app communicates with an external user and internal web server.
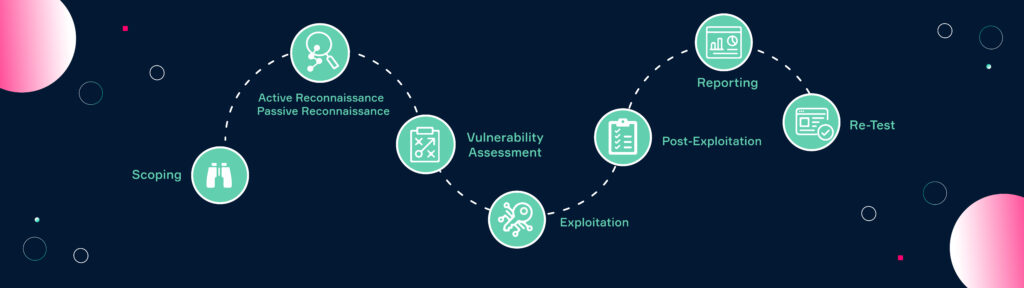
Pentesting a web app follows the same structure as all penetration tests. The pentesting stages are:
- Scoping: Define the objective of the penetration test.
- Reconnaissance: Gather passive information (OSINT) and active information about the target.
- Vulnerability Assessment: Identify and assess potential vulnerabilities.
- Exploitation: Attempt to exploit identified vulnerabilities to gain unauthorized access.
- Post-exploitation: Evaluate vulnerabilities and their impact.
- Reporting: Document the findings and how to fix them in a detailed report.
- Retesting: Recheck vulnerabilities to ensure they have been fixed.
For more details about the stages of penetration testing, check out “What is penetration testing?“.
What does a web application penetration test check?
A web app penetration test looks at the security of a web application holistically. This includes topics such as authentication & authorization mechanisms, input validation, configuration management, and more. The most well-known approach to test a web application is the OWASP test procedure (Open Web Application Security Project).
The OWASP foundation is an NGO that has set itself the task of increasing the IT security of software. The OWASP Foundation primarily offers methodological content on the topic of web application security and regularly publishes a test guide for penetration tests of web apps and mobile apps. They also publish the most common vulnerabilities of web applications.
OWASP Top 10 – Vulnerabilities in Web Applications
- Broken Access Control – Allows users to access resources or functions they should normally have no access to.
- Cryptographic Failures – Failures in encryption are leaving sensitive data and communication exposed.
- Injection – Data supplied by users is insufficiently validated enabling them to inject scripts.
- Insecure Design – The design architecture of the web app itself has significant flaws leading to vulnerabilities.
- Security Misconfiguration – Unnecessary features or missing security hardening that pose a security risk.
- Vulnerable and Outdated Components – Out of date software that is known to be vulnerable to attacks.
- Identification and Authentication Failures – Weak passwords or authentication that permits automated attacks.
- Software and Data Integrity Failures – Source for automated updates is not verified leading to abuse by attackers.
- Security Logging and Monitoring Failures – Inability to properly log and monitor security-related events.
- Server-Side Request Forgery – Allows attackers to send their own unauthorized requests via web applications.
Beside the top 10 list, there are many other vulnerabilities a penetration tester should consider. But to keep it simple, we are focusing on the most well-known ones. For this reason, we have selected two of the top three most common vulnerabilities, Broken Access Control & Injection, for a more detailed explanation.
Broken Access Control
Broken access control is also known as authentication and authorization error. It describes a vulnerability that enables unauthorized users to have access to content that should normally be restricted.
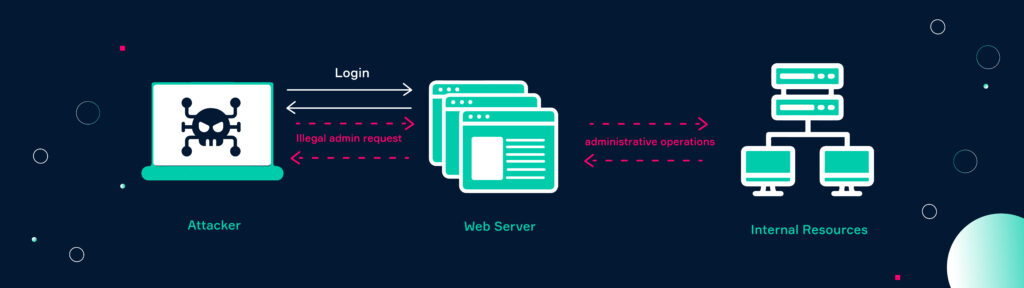
During a test, a cyber security expert verifies if an underprivileged user can get higher access permissions than originally embedded in his role. In practical terms, this could mean that an attacker can exploit the rights of an admin to reset user passwords. He could then reassign them and gain access to accounts or sensitive data.
Injection
To increase the security of a web application, it is necessary to validate client-side requests. Otherwise, a client can send manipulated requests to the server to inject code with the aim of controlling the server’s response. Popular injection attacks include cross-site scripting or SQL injection. The risk of an injection attack can be significantly reduced by a server-side security check.
Which tools are used in a web application penetration test?
To test a web application, penetration tester deploy a variety of automated tools. These automated tools have three main purposes:
- Information gathering about the target IT infrastructure such as ports, IPs, etc.
- The scanning for potential vulnerabilities that need further analysis.
- Potentially automated exploitation of vulnerabilities
It is important to understand that these automated tools should never be seen as a substitute for an actual pentest. They should be seen as a tool for professionals that significantly helps them in identifying potential vulnerabilities for further testing. As a surgeon needs a good scalpel, a penetration testers needs good pentesting tools.
Popular and widely used software tools for web application penetration tests are web app scanner and proxys, like ZAP and Burp suite. In addition, tools for SQL Injection vulnerability identification and exlpoitation like SQLMap come into play. Read the next paragraph to get a better understanding of what these software tools do in detail.
Web Application Scanner and Proxy
Web Application Scanner allow automated scans and exploitations for vulnerabilities and attack vectors. They map the entire structure of a website. Based on the data collected, the scanner can try to exploit the vulnerabilities automatically.
Popular scanning tools for web applications are the free open-source program OWASP ZAP (Zed Attack Proxy) and the payed software Burp Suite. The main functions of both programs are:
- Automated scans – Scanning web applications for typical vulnerabilities.
- Manual scans – Identifying security loopholes with a manual scan.
- Proxy Server – Intercepting, checking and manipulating HTTP- and HTTPS- requests and responses.
- Fuzzing – Sending unvalidated and unexpected requests to a web server.
Both tools are important to improve a web application’s security as they make the test procedure more efficient. Burp Suite can be seen as the industry standard for web app pentesting toolkits and is, therefore, used very frequently.
Tools for Identification and Exploitation of SQL-Injections
Next to Cross-Site-Scripting (XSS), especially SQL-Injections are popular among cybercriminals when it comes to compromising a web application. A widely used Programm for automated detection of SQL-Injection vulnerabilities is SQLMap.

These are its most important features:
- Automated Tests – Execution of automated tests in order to search for SQL-Injection vulnerabilities.
- Multiple data bases – Data base search such as MySQL, Oracle, MicrosoftSQL server, and PostgreSQL.
- Read data bases – Extraction of usernames, passwords and tables from databases / reading the entire data base.
- Support of proxy servers – Usage of proxy servers in order to track and check the traffic between web app and tool.
- Reporting– Generation of automated summaries for detected SQL-Injection vulnerabilities.
These functions make SQLMap a powerful tool for any pentester performing a web app penetration test.
Conclusion
A web application penetration test can reveal crucial security gaps in the application design and its underlying network infrastructure. In terms of content, the web app pentest checks various potential vulnerabilities, such as faulty authentication and authorization of the application.
The repertoire of every penetration tester should include the programs OWASP ZAP, Burp Suite, and SQLMap. All three programs automate a specific part of the pentest and increase the efficiency of the testing process. In this context, the OWASP Foundation has published a generally accepted methodology for web app pentests and also provided a list of the most frequently encountered vulnerabilities in recent years.
With the growing threat of cybercrime web application penetration test should be an integral part of the software development lifecycle. This can save organizations from severe financial losses and reputational damage.
