Penetration testing or ‘pentesting’ is a simulated cyberattack performed by authorized cybersecurity experts with the goal to identify vulnerabilities in IT infrastructures, applications, and networks. Pentesting is a structured approach to ethical hacking. It is the best way to test the cyber resilience of a company as it provides a detailed analysis about identified vulnerabilities, their impact, but also a guide on how to fix them.
Unlike classic preventative IT security measures such as antivirus software, firewalls, and automated scanners, penetration testing is a deep-dive and true test, if for example an app can withstand a cyberattack. This is why many industries, such as fintech, are required by law to perform pentests on a regular basis. Not surprising as for instance errors in the authentication of users in a banking app could potentially cause major harm to thousands of people.
Thus, a bank invests preventively in the security of customer data instead of risking reputational damage and significant financial losses. Considering that 84% of all German companies have been affected by cyber attacks in 2022, it becomes evident that preventive measures, such as a penetration test, are essential.

Why is penetration testing necessary?
Penetration testing significantly reduce the success rate and impact of cyberattacks. Cyberattacks are the attempt to compromise the security of an IT system, network, or application. Most common cyberattacks are:
- Phishing – Most commonly occurring via email, is a fraudulent message that attempts to trick their recipient into installing malicious software or disclosing information, such as login credentials.
- Misconfiguration and software vulnerabilities – Security relevant misconfigurations and software vulnerabilities can build the foundation for a malicious attack.
- DoS – Denial of Service (DoS) attacks intent to overload a server with request to cause service disruption or breakdown. This type of attack are especially harmful for online-facing industries such as e-commerce.
In 2022, cyberdamages have caused €203 bn damages in the German market alone. Less than 30% of incidents have been resolved. In 2021, the German county ‘Anhalt-Bitterfeld’ declared a cyber emergency state for the very first time in German history. The reason was a cyberattack which led to 100,000 people without social services like unemployment benefits.
Penetration tests prevent many cyberattacks from being successful. They increase resilience of systems and networks. Meaning that even if a cyberattack has been successful in one area it might not be able to spread to another. For parts of critical infrastructure, like the healthcare sector, public administration, or financial institution it is mandatory to conduct pentests annually. This is due to the disproportionally high negative impact caused by a downtime in these areas.
Is penetration testing safe?
Penetration testing is safe. At least if done correctly. Pentests follow a strict scoping process that ensures no mistakes happen. This does not mean that mistakes can’t happen, which is why preparation is key:
- Penetration testing vendors and experts should be carefully selected.
- The project properly planned and potential risks addressed.
- Security measures such as backups and testing environments considered.
We also, recommend to work with pentesters who are OSCP (Offensive Security Certified Professional) certified. Pick pentesting vendors that have a track record and references that you can verify. Also, we recommend to select vendors in your jurisdiction.
What penetration testing methods exist?
Penetrationtests can be executed in three different ways: White Box, Grey Box, and Black Box. These methods mainly differ in terms of how much information is made available to an expert running the test. The more a pentester knows about a target, the less authentic a test gets. This is due to the fact that in the real world hackers do not have this information at hand and might attack a system or network differently. Hence, all three methods have their own unique purpose and benefits.
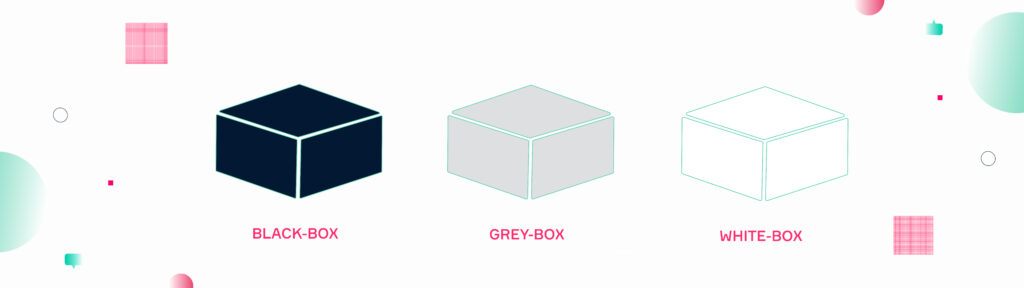
Black Box
The black box method is a zero knowledge approach. Pentesters receive a target system, software, or network that needs to be tested. In this scenario a pentester has the same starting point as a potential malicious actor. Black box tests are particularly useful when a company wants to test their IT from an outsiders perspective.
The black box method is the least efficient pentesting approach as it requires a lot of time spend on research. The risk of the black box approach, however, is that potential vulnerabilities or attack vectors might remain undetected or are considered out of scope.
White Box
The white box method is the all knowledge approach. Here, the penetration testers receive all necessary information about e.g. infrastructure, servers, and applications before the test starts. This makes it possible to run small, very targeted test, which is especially useful for software development. This makes the White Box approach the least realistic test scenario, as the pentester has a considerable knowledge advantage.
A white box test scenario is suitable for the extensive assessment of applications e.g. via a source code review. It is the most efficient way to identify vulnerabilities. In many cases companies are reluctant to provide all information required though, which is why they pick the grey box method.
Grey Box
A combination of the black box and white box method is known as grey box. The idea of the grey box approach is that neither zero nor all knowledge are the best way to approach a test as they are either very realistic but less efficient or very efficient but less realistic. Thus, the grey box method creates a balance between efficiency and authenticity. Similar to the White Box Approach, the Grey Box test allows to focus on specific targets through the initial information advantage. Access credentials for these systems can be provided in advance.
The Grey Box approach is also useful, if specific critical systems should be excluded from the test. In reality this scenario is common, because organizations are reluctant to share the source code of an application (White Box) for instance, but want to preserve the highest possible authenticity of the pentest.
How does penetration testing work?
The process of penetration testing can be broken down into five stages: scoping, reconnassaince, vulnerability assessment, exploitation, post exploitation, and reporting. These different stages give a penetration test structure, ensure that a test follows a pre-defined path, and provides the desired results. Depending on the test type and the quality of the pentesting provider a penetration test also has a re-testing stage to ensure that identified vulnerabilities have been closed.
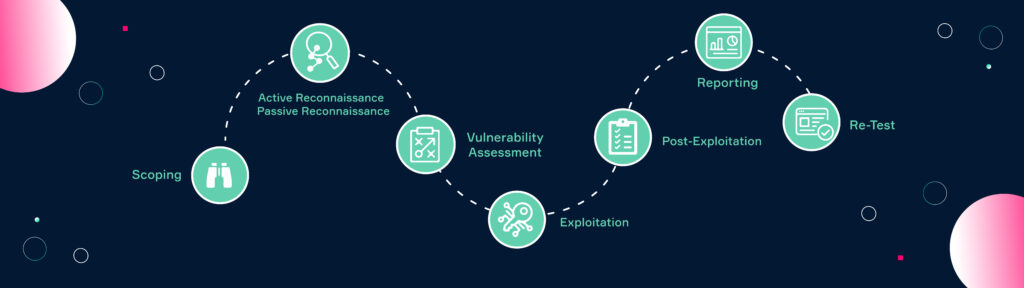
Scoping
Scoping is the first and most important stage for all penetration tests. In this stage the pentester and client meet to discuss the method and type of test. The test is then tailored to the customer’s requirements. This is crucial as all parties need to have the same understanding on what the test is trying to achieve.
Scoping topic examples:
- Method
- Type
- Timeline
- Test duration
- Targets
As for everything good preparation is key and a professional pentesting provider will be able to address and discuss all potential issues that might arise throughout a penetration test.
Reconnaissance
After the cornerstones of the test have been established, the reconnaissance starts. In this stage, the pentester gathers and evaluates information about its target to plan the attack paths. Reconnaissance can be divided into two phase: passive and active reconnaissance.
Passive Reconnaissance
Passive reconnaissance refers to the acquisition and evaluation of publicly available information. This procedure is also known as OSINT (Open-Source Intelligence). Within the context of OSINT, print media, public data bases, websites or even social media channels can be used to gather data.
The goal is to acquire initial technical as well as structural information about the target to determine what potential vulnerabilities might exist. Technical information can be, for example IP addresses, domain names or e-mail addresses. Structural information includes names of employees or internal hierarchies. At the end of the reconnaissance, all relevant information is evaluated. This step is not required for a White Box Test, as the client provides all necessary information in advance.
Active Reconnaissance
Active reconnaissance involves the pentester interacting directly with their target. For this purpose, automated scanners are deployed to gather information about available/open ports, operating systems, and applications. This stage provides penetration testers a detailed overview about their target. It serves the purpose of identifying and providing a pre-assessment of potential weaknesses that need further analysis.
Vulnerability Assessment & Scanning
The vulnerability assessment stage builds on the information acquired in the reconnaissance stage. Vulnerability scanners (automated penetration testing) are deployed to analyze target systems and applications identified in the reconnaissance stage. They provide the foundation for a pentester’s manual work as the pentester utilizes the information to proceed into the exploitation stage.
It is important to mention that properly understanding and acting on the results of vulnerability scanners requires expert knowledge. These automated vulnerability scanners have the tendency to provide many false negative results and can only scan their target on the surface level. Trusting the assessment of automated scanners in this stage can lead to a false sense of security.
Exploitation
The exploitation stage of a penetration test is where the penetration tester attempts to exploit the vulnerabilities identified during the reconnaissance and scanning stages to gain unauthorized access to a target system, network, or application.
During this phase, the penetration tester may use various techniques and tools to gain access to the system, such as:
- Password cracking: The tester may use automated tools to guess or crack weak passwords to gain access to user accounts.
- Social engineering: The tester may attempt to manipulate individuals within the organization to gain access to sensitive information or to obtain credentials that can be used to access the target system.
- Exploiting software vulnerabilities: The tester may attempt to exploit known or new vulnerabilities in software applications, operating systems, or network devices to gain access to the target system.
- Privilege escalation: Once the tester has gained access to the system, they may attempt to escalate their privileges to assess if they could gain administrative access and full control.
The exploitation stage is a critical part of the penetration testing process, as it provides valuable insights into the effectiveness of the target system’s security controls and highlights areas where the system may be vulnerable to an attack. The goal of this stage is to identify and exploit as many vulnerabilities as possible, in order to demonstrate the potential impact of a successful attack and to help the client prioritize remediation efforts.
It’s worth noting that the exploitation phase should only be conducted with the client’s explicit permission and under controlled conditions to minimize any potential impact on the target system’s availability, integrity or confidentiality.
Post-Exploitation
The exploitation phase is followed by the post-exploitation phase. The identified vulnerabilities are examined and graded based on their accessibility, impact, and severity.
- How easy can a vulnerability be exploited? Here, the probability with which the a vulnerability can be exploited is classified. Influencing factors are, for example: the public accessibility or the skills required.
- How impactful is the vulnerability? Not all vulnerabilities are equal as some might provide access to the IT infrastructure or critical assets, causing huge revenue losses and other only scratch on the surface level.
- How critical is the vulnerability? It is important to distinguish how a vulnerability might affect an organization specifically. A vulnerability might provide access to the entire manufacturing line or intellectual property.
By identifying vulnerabilities and demonstrating their potential consequences, organizations can better understand the risks they face and take steps to mitigate them. At the end of the post-exploitation stage, the pentester concludes the actual test and starts to write the reporting.
Reporting
The primary goal of the reporting stage is to provide a clear, concise, and comprehensive overview of the vulnerabilities identified, the potential impact of those vulnerabilities, and recommendations for remediation.
The report typically includes the following elements:
- Executive summary: An overview of the test, including the scope, methodology, and key findings.
- Technical findings: A detailed description of each vulnerability discovered, including the severity of the vulnerability, the steps taken to exploit it, and the potential impact on the organization.
- Remediation recommendations: Guidance on how to mitigate each vulnerability discovered, including steps to remediate the vulnerability and best practices for improving overall security.
The report may also include supporting documentation, such as screenshots, log files, and other evidence of the vulnerabilities discovered. The goal of the report is to provide actionable information that can be used to improve the security of the organization and mitigate the risks identified during the penetration test.
Retesting
A retest often is a follow-up test that is conducted after the initial penetration testing has been completed and remediation measures have been implemented. The purpose of a retest is to verify that the identified vulnerabilities have been effectively remediated and to confirm that the security measures implemented by the organization are adequate to protect against similar attacks in the future.
During a retest, the same penetration testing methodology and tools may be used. The retest may focus specifically on the vulnerabilities that were identified during the initial test or may encompass a broader range of security assessments to provide a more comprehensive evaluation.
In recent years, modern pentesting vendors started retesting of identified vulnerabilities as part of the testing process to accelerate the fixing of vulnerabilities.
Which types of penetration testing exist?
Penetration testing is a type of security assessment that involves identifying vulnerabilities in an organization’s systems, applications, and network infrastructure. There are several types of penetration testing, each of which focuses on different areas of an organization’s security posture.
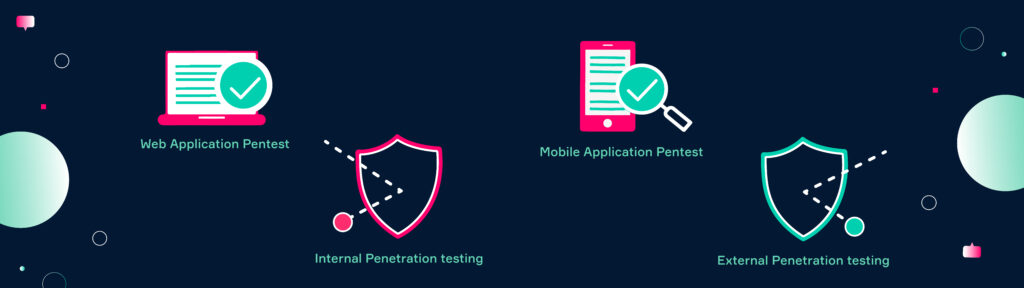
The specific type of penetration testing chosen will depend on the organization’s needs, the scope of the testing, and the specific security risks faced by the organization. We’ve selected four typical pentests for further explanations:
Web Application Pentest
A web application is a type of software program that runs on a web server and can be accessed over the internet through a web browser. Web applications are designed to provide users with a specific set of functions or services, such as online shopping, social media, or online-banking.
Because web applications are accessible over the internet, they can be vulnerable to attacks such as SQL injection, cross-site scripting (XSS), authentication bypass, and other types of vulnerabilities. As a result, it is important to ensure that web applications are designed and implemented with security in mind.
For this reason, it is especially important for online-facing businesses, such as e-commerce and online banks, to perform penetration tests on their web application to prevent cyber incidents. Operational breakdowns of an online shop due to a cyberattack for instance would cause significant financial harm to the organization. These types of businesses are also very dependent on public trust and all-time availability, making them an attractive target for malicous actors.
Mobile Application Pentest
Mobile applications are programs that run on mobile devices. They can be vulnerable to attacks such as insecure data storage, insecure communication, and local privilege escalation.
Penetration testing for mobile apps tests the stability and security of said apps. A pentest is possible for native iOS and Android apps. During the test, emphasis is paid to parameters such as personal messages, movement profiles, location data, and other critical user data that would have devastating effects in case of a data breach.
Mobile application pentests are especially important for companies that handle private and financial data or where the app is essential for their business. Pentests are, therefore, recommended during or directly after app development and when important updates occur.
External Penetration testing
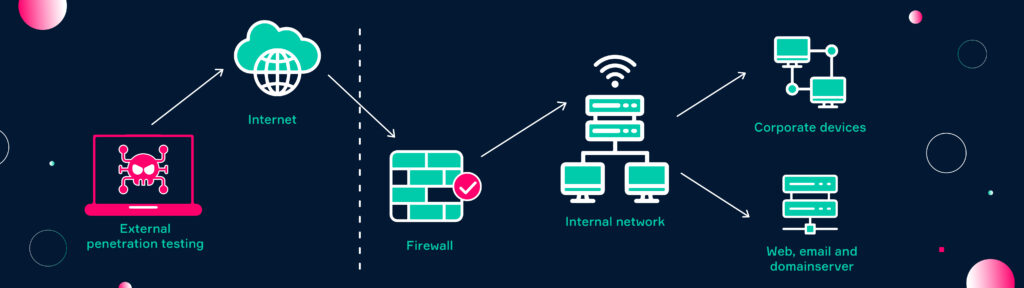
External penetration testing is used to evaluate an organization’s external-facing systems and network infrastructure. External-facing systems include those that are accessible over the internet, such as web servers, email servers, and VPN gateways. During an external penetration test, the tester will identify vulnerabilities in these systems and attempt to exploit them in order to gain unauthorized access to the internal network.
Internal Penetration testing
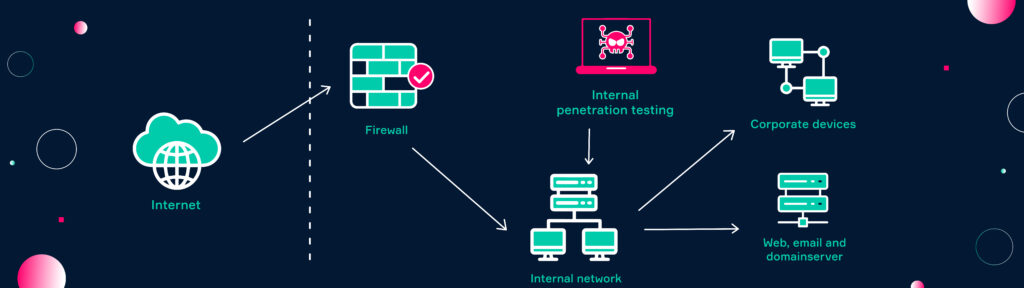
Internal penetration testing is used to evaluate an organization’s internal systems and network infrastructure. An internal pentest simulates an attack in which an attacker already has gained access to the internal network, for example through a compromised client.
Internal systems include those components that are accessible only from within the organization’s network, such as file servers, databases, and workstations. During an internal penetration test, the tester will identify vulnerabilities in these systems and attempt to exploit them. Thus, evaluating what damage an attacker could do after getting internal access.
Devices such as service laptops or internal applications are often the first point of entry for an external attacker and are therefore the focus of most penetration tests performed internally.
Which tools are used in a penetration test?
To perform a pentest, penetration testers deploy a variety of automated scanning tools. These automated scanning tools have two main purposes:
- Information gathering about the target IT infrastructure such as ports, IPs, etc.
- The scanning for potential vulnerabilities that need further analysis.
It is important to understand that these automated tools should never be seen as a substitute for an actual pentest. They should be seen as a tool for professionals that significantly helps them in identifying potential vulnerabilities for further testing. As a surgeon needs a good scalpel, a penetration testers needs a good scanning tools.
Some of the more commonly used and highly popular scanners are Nmap or Metasploit. Let’s have a look at what they do.
Nmap
Nmap (Network Mapper) is a popular open-source network exploration and security auditing tool. It is used for scanning and mapping networks, identifying hosts and services running on a network. Nmap uses various scanning techniques such as TCP, UDP, FIN, and Xmas Scan to determine the availability of network hosts, the open ports, and the services running on those ports. It also supports various advanced features like OS and version detection.
As Nmap provides various information about the state of ports. This is particularly interesting for penetration testers as they can assess if a port is open and which service is running behind it. This allows potential vulnerabilities to be identified as part of the reconnaissance stage in a pentest.
Nmap can assign the following parameters to ports:
- Open
- Closed
- Filtered
- Unfiltered
- Open and filtered
- Closed and filtered
An open port means that the target is ready to accept data flows via TCP or UDP connections. The port accepts these data packets and then offers the requested service. Open ports are always a potential attack surface for cybercriminals. A network should therefore only have the minimum required number of open ports.
With closed ports, no communication is possible. This implies that no application is accepting TCP or UDP data packets in the background. If a port is shown as filtered, either no response comes via the TCP or the port is blocked by a firewall. The state “unfiltered” means that it cannot be clearly checked whether the port is open or closed.
Metasploit
As a open-source framework, Metasploit offers an entire toolbox for pentesting. The tool enables penetration testers to test the security of networks and computer systems by simulating various attack scenarios. Some of the features are automated exploitation, advanced payloads, and post-exploitation modules.
Metasploit is used for building an attack plan for vulnerability exploitation. It offers access to a large database of exploits that are not only valuable for pentesters but also researchers. It requires extensive knowledge to properly operate and should therefore only be used by certified security professionals. This does not keep some malicious actors to use this tool for their own purposes though.
Only if the penetration tester can penetrate a system via a vulnerability, its status as a vulnerability is confirmed. Used correctly, both tools, Nmap and Metasploit, can be very helpful for a penetration tester.
What are the benefits of penetration testing?
Penetration tests provide the opportunity to assess the security of your IT from an attacker’s perspective. Depending on the chosen approach, a penetration test comes very close to a realistic hacking attack. A pentest is an evaluation performed by a neutral and professional third party that comes with several benefits:
- Identifying vulnerabilities: Penetration testing helps identify security vulnerabilities that may be present in the system, network, or application. This helps organizations address these issues before attackers can exploit them.
- Measuring the effectiveness of security measures: Penetration testing can help organizations determine the effectiveness of their existing security measures and identify areas for improvement.
- Compliance with regulations: Many regulations and standards, such as PCI DSS, HIPAA or ISO 27000 require organizations to perform regular security assessments. Penetration testing can help organizations meet these compliance requirements.
- Avoiding financial losses: Penetration testing can help organizations avoid financial losses due to security breaches. By identifying vulnerabilities and addressing them, organizations can prevent cyber attacks that could lead to revenue losses or fines.
- Protecting reputation: A security breach can damage an organization’s reputation. Penetration testing can help organizations prevent such incidents and maintain their reputation. A regular repetition also strengthens the trust of customers and partners.
- Providing insights: Penetration testing can provide insights into the security posture of an organization, helping them to make informed decisions about their security strategy and investments.
How often should a penetration test be conducted?
IT security is dynamic process. Most security experts recommend conducting penetration testing annually, as part of a comprehensive security testing strategy. But it is also recommended to perform penetration tests when
- … significant changes occur in the IT infrastructure.
- … novel threats are identified and could pose a risk.
Some industries are required by law to perform penetration tests, such as organizations that are a part of the critical infrastructure (in Germany: KRITIS). Penetration tests are also mandatory to meet DSGVO requirements, and other compliance regulations.
How much does a pentest cost?
Penetration tests are individually tailored to the requirements of an organization. Three factors significantly influence the pricing:
- Complexity – Project planning efforts to design and run the test
- Duration – Size of project and project execution time required
- Difficulty – Difficult projects required more experienced testers
The pricing can also vary based on the penetration testing type. An external penetration test typically costs less than an internal one. With that said, the pricing of a penetration test can be roughly separated into five pricing ranges:
- Tiny test (Days: 0,5-2 | Price range: €750 – €4,000)
- Small tests (Days: 2-5 | Price range: €2,500 – €10,000)
- Medium tests (Days: 5-10) | Price range: €7500 – €20,000)
- Large test (Days: 10-15) | Price range: €12,500 – €30,000)
- Enterprise tests (Days: >15 | Price: TBD)
Note: The prices refer to manual penetration tests.
The costs of penetration tests can be significantly reduced by booking larger quantity of pentesting days in advanced. These recurring pentesting packages can be booked on a yearly or quarterly basis.
Community-powered penetration testing
Every real hacker acts individually when performing a cyberattack. For this reason, it is advisable to change the penetration testers on a regular basis. Modern providers of penetration tests use a freelancer community for this reason, instead of repeatedly relying on the same employees.
This maximizes the security of an application, system or network, as different approaches from different penetration testers ensure the highest possible fidelity to reality.
Final thoughts
The penetration test is an important element in the fight against cybercrime. As a preventive measure, it can make a decisive contribution to the cyber resilience of an organization. Penetration testers simulate a realistic attack on a system, an IT infrastructure, or an application.
The vulnerabilities identified can then be remediated. In contrast to an automated vulnerability scan, the penetration test offers an in-depth, realistic analysis of an application or network. In this way, organizations can approach IT security actively instead of waiting passively for a real attack, hoping that the measures taken are sufficient.
Modern providers of penetration tests also offer their customers a broadly diversified community of penetration testers. This approach enables the individuality of a real hacker to be reflected in the attack simulation.
For parts of the critical infrastructure, for complying with DSGVO requirements and for ISO certifications, penetration tests are mandatory and must be repeated regularly.
